To get to this page, to to Services → SMTP Server → Spam Reduction and press the Edit Realtime Blacklist Rules button.
Note that this option is only available in VPOP3 Enterprise.
Realtime Blacklists
Realtime Blacklists (RBLs) are DNS-based databases which contain lists of IP addresses known to be used for sending spam, or known to be compromised with 'bots' or which are not meant to send email messages directly. These blacklists can change dynamically over time, so the data doesn't need downloading or synchronising.
VPOP3 can check these RBLs for incoming SMTP messages. You should only use it if the incoming SMTP is directly to your VPOP3 server. If the messages are coming through a third-party service (eg a queuing service or filtering service) before reaching VPOP3, then do not check RBLs. All the messages will appear to come from the third-party service, not the sender, so checking the sender IP address will be useless and will just slow things down.
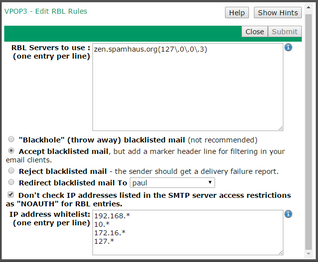
In the RBL Servers to use box, enter the names of the RBL services to use - eg 'zen.spamhaus.org' or 'dnsbl-2.uceprotect.net', etc.
VPOP3 will look up the IP address of the incoming sender in all the specified lists to determine if the sender is blacklisted. The blacklist will return an IP address for the name which VPOP3 looks up. By default, VPOP3 will treat the IP address as blacklisted if the blacklist returns any IP address at all (as opposed to 'name not known')
So, if you have zen.spamhaus.org, and there's an incoming connection from IP address 1.2.3.4, VPOP3 will do an A record DNS query for 4.3.2.1.zen.spamhaus.org. If that DNS lookup returns a value, then VPOP3 will treat the sender as blacklisted.
From VPOP3 v6.17 onwards you can also specify a regular expression which must match the returned IP address for the sender to be blacklisted. To do this, specify the regular expression in parentheses immediately after the RBL name (without any spaces). For example, in the screenshot above, VPOP3 will do a DNS query to zen.spamhaus.org, and if the returning IP address matches the regular expression 127\.0\.0\.3 then the sender will be treated as blacklisted. If any other result (or no result) is returned, then it won't be treated as blacklisted. This can be useful for some RBLs (such as zen.spamhaus.org) which return different values depending on the IP address status.
Below the RBL Servers to use box, are various options to indicate what VPOP3 should do with messages from blacklisted senders:
•Blackhole blacklisted mail - the message will be accepted by VPOP3 and then simply discarded. The sender will think the message was delivered, but it will not be. We do not recommend this option because it can cause confusion if a sender is on an RBL and doesn't realise it. Instead, if you do not want to receive the message, use the Reject blacklisted mail option instead.
•Accept blacklisted mail - VPOP3 will accept the messages and deliver them as normal. However, it will add a header beginning with the text X-RBLFound, such as
X-RBLFound: Sender address A.B.C.D found in RBL entry on YYYYY
•Reject blacklisted mail - VPOP3 will do an SMTP reject on the message. The sending mail server should send a delivery failure report to the message sender. The SMTP rejection message from VPOP3 says:
550 5.7.1 Mail not allowed because client address A.B.C.D found in RBL entry on YYYYY
•Redirect blacklisted mail to ... - VPOP3 will accept the messages, but will deliver them to the specified user, instead of the original recipient.
If the Don't check IP addresses listed in the SMTP server access restrictions as "NOAUTH" for RBL entries option is checked, then VPOP3 will look at the service's IP Access Restrictions and if the sender IP address is listed as "Allow Unauth" or "Allow Unauthenticated Access", then VPOP3 will skip the RBL checking.
The IP address whitelist lets you specify IP addresses (using wildcards if desired) which will make VPOP3 not perform RBL checking, eg 192.168.* will make VPOP3 not perform RBL checking for any IP address beginning with "192.168."
Note that the SMTPSVR Lua script lets a script modify the RBL checking behaviour and see the results using the "Start()" and "RBLResults()" functions.