
To get to this page, go to Settings → Security Settings -> General.
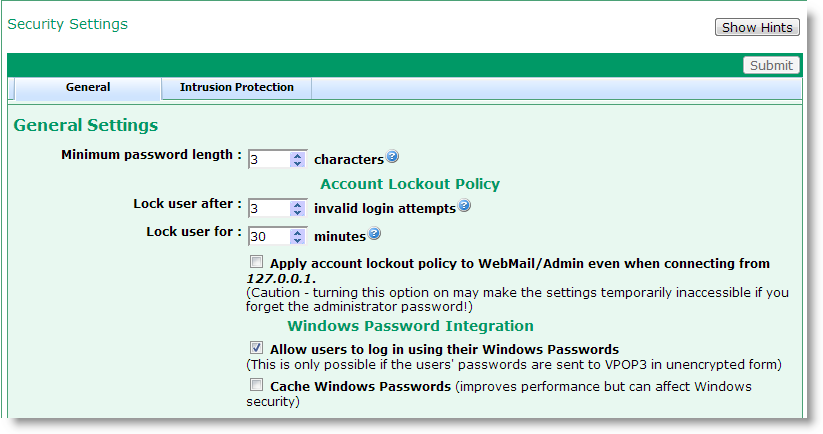
The Minimum Password Length option sets the length (in characters) of the shortest password which can be set. This only applies to passwords set after this setting has been changed.
Account Lockout Policy
If someone tries to log into an account and specifies an incorrect password several times in a row, then VPOP3 will lock access to the account from that IP address for a short time. This is to make password attacks harder. The user will not be told that the account has been locked; they will just be told that the login failed, even if they enter the correct username & password.
VPOP3 will only lock access from the IP address which had the failed login attempts. This is to prevent someone deliberately failing login attempts to cause a denial-of-service (DoS) attack.
You can tell if an account is locked because the Users list will display a padlock icon to the left of the account name. You can unlock an account by editing the account, and clearing the Account Locked checkbox on the User's General tab.
The Lock user after x invalid login attempts setting tells VPOP3 how many failed login attempts are allowed before the account is locked.
The Lock user for x minutes setting tells VPOP3 how long to lock the account for once the allowed failed login attempts has been exceeded. Once this time is up, then the account will automatically unlock itself.
If the administrator account is locked, and you cannot wait the specified time for the account to unlock, then you can restart the VPOP3 service to force all the account locks to be removed. You can also try accessing the VPOP3 settings from the VPOP3 PC itself (see below). |
Normally, VPOP3 will not lock out accounts if they are accessed from the TCP/IP loopback address (127.0.0.1). This is to always allow administrator login from the VPOP3 computer itself. This assumes that the VPOP3 PC is physically secures so that hackers cannot gain access to it, and also cannot gain access via remote-desktop or other remote control software. The Start » Programs » VPOP3 » Configure VPOP3 link in the Windows menus will access the VPOP3 settings using the loopback address.
If you wish VPOP3 to apply the lockout policy to the loopback address as well, you can check the Apply account lockout policy to WebMail/Admin even when connecting from 127.0.0.1 option. However, note that doing so may make it much harder for a legitimate administrator to gain access to VPOP3's settings if they are unsure of the login password.
Windows Password Integration
VPOP3 has its own user database system. It is not linked into a Windows user database such as Active Directory. This is for several reasons. For instance:
❖VPOP3 will run on any version of Windows, not just Windows Server versions. If VPOP3 required the Windows user database, then installation on desktop versions of Windows could be troublesome.
❖Some email authentication methods would not be available if VPOP3 only used the Windows user database because of how Windows allows third party programs to access the user database.
❖Many times users do not want the email passwords to be linked to their Windows passwords. Often email passwords are configured into an email client and are not changed, but Windows passwords may expiry regularly.
However, VPOP3 has some features which may help with installations where people want to be able to use Windows login details to access VPOP3. To use these features, VPOP3 needs to know the Windows username relating to the VPOP3 username. In the simplest case, the VPOP3 usernames and Windows usernames will be identical. If that isn't the case, then the administrator can set the Windows username for a VPOP3 user in the user's Advanced tab.
If the Allow users to log in using their Windows passwords.option is checked, then VPOP3 will allow users to log in using either their VPOP3 login details, or their Windows passwords. Note that VPOP3 can only check passwords against the Windows user database if VPOP3 receives them in plain text. Hashed passwords, such as CRAM-MD5 passwords cannot be checked against the Windows user database. To avoid sending Windows passwords in plain text across the network you should consider using session encryption (requires VPOP3 Enterprise).
If the Cache Windows passwords option is checked, then, if VPOP3 detects that a user has entered their Windows password, VPOP3 will update its own user database to match the same password that the user entered. This will invalidate the previous VPOP3 password. We do not recommend the use of this option because the encryption method which VPOP3 uses for storing the passwords may not be as secure as the method which Windows uses, meaning that storing the passwords in a possibly less secure database may compromise security.

